Bugs_BunnyCTF 2k17
Bugs_Bunny CTF 2k17 - International edition
This was our first experience to host a capture the flag contest.
In this contest we are delighted to share our passion and experience by offering a several missions and challenges like web exploitation, forensics,steganography,cryptography, etc.. in order to make challengers improve their skills when they having fun. Together we will dive challenger in a digital world where they have to conquer other skilled teams and one team shall be crowned.
This challenge was for 24h of competition between challengers also it was a real challenge for us to maintain our 5 servers up and on line against hackers want to gain an access on our servers and others want to shutdown our server using attacks like DDOS attack.
Fortunately none of hackers can gain access on our servers, but unfortunately some of hackers who want to shutdown our servers they succeed to make the latter freezing and in some situations we were obliged to reboot the server.
Next year we will be more attentive in the setup of our server, to maintain all DDOS attack without any freezing in our server or reboot need.
All this happened thanks to this greate team which is composed of:
-Aymen Borgi
-Bilel Korbosli(BilKor)
-Chouaib hammami
-Fakhri Mabrouki
-Iheb ben salem(Sold1r)
-Mohamed chamli(TnMch)
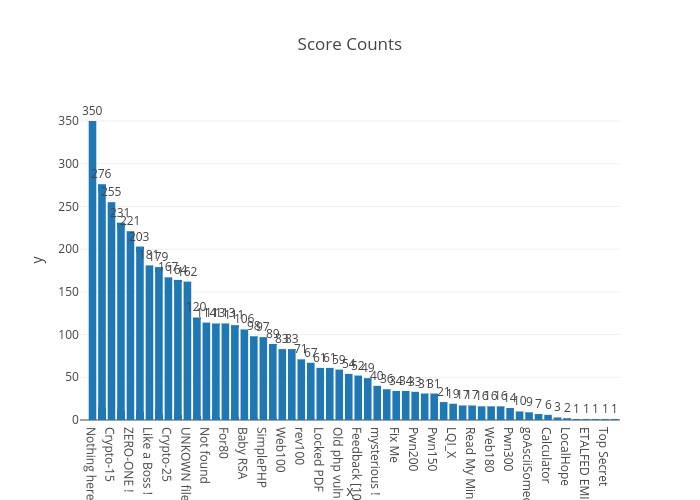
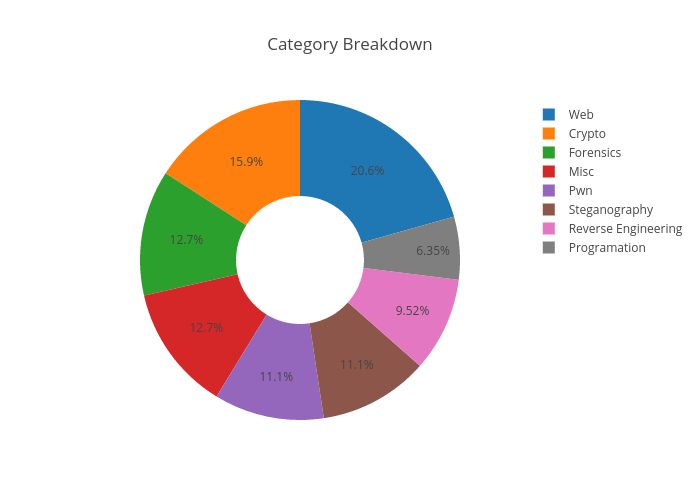
Here is some statistics
We have created more than 50 tasks from easiest to hardest.
Feedbacks about the contest
Feedbacks from ctftime.org ?!
Participate again in the CTF ?!
Write-ups links
https://advancedpersistentjest.com/2017/07/31/writeups-rev75-simplephp-pwn100-bugs-bunny-ctf/
https://aadityapurani.com/2017/07/30/bugs-bunny-ctf-writeups/
https://st98.github.io/diary/posts/2017-08-01-bugs-bunny-ctf-2k17.html
Hopefully see you next year, in the second edition of Bugs_BunnyCTF with many new and exciting challenges and many others surprises.
Goodbye.






















































2 comments: